Identity and access overview report documentation
Assess the security of your user accounts across multiple cloud providers.
About this report
Root out excessive permissions and risky account configurations before they lead to security incidents. Security teams can identify over-privileged users, dormant accounts, and authentication weaknesses across multiple cloud providers from a single dashboard.
Key questions
- Who has too much access to our cloud environments?
- Which user accounts pose the greatest security risk?
- Are we following access management best practices?
- How can we reduce privilege escalation risks across our cloud accounts?
Visualizations in the report
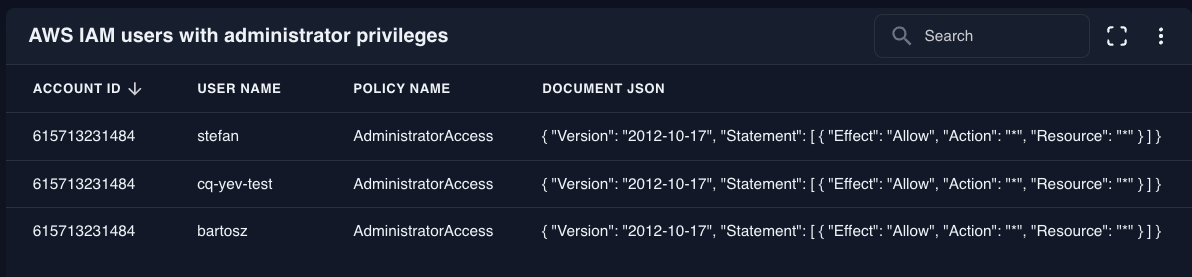
AWS IAM users with administrator privileges
Counts accounts with full control permissions in AWS. These powerful accounts should be strictly limited and closely monitored.
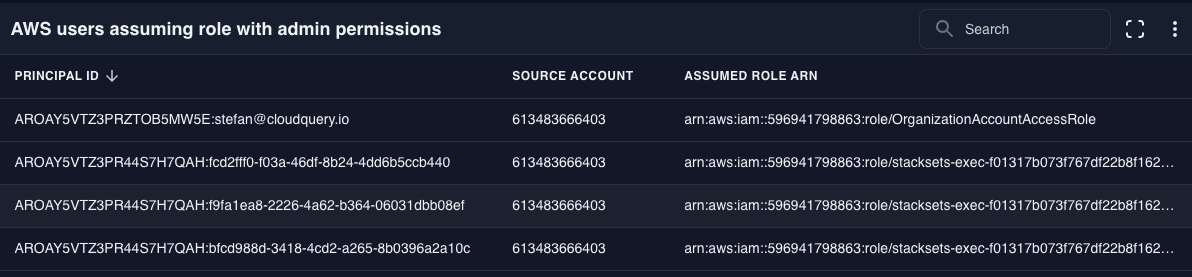
AWS users assuming a role with admin permissions
Reveals which users are obtaining elevated privileges through temporary role assumption. Identify potential privilege escalation paths that might bypass normal security controls.
AWS IAM inactive users
Lists dormant accounts that should be disabled or removed. These unnecessary accounts increase your attack surface without business benefit.
AWS users without MFA
Shows accounts missing crucial multi-factor authentication protection. These accounts are at much higher risk of credential theft and account takeover.
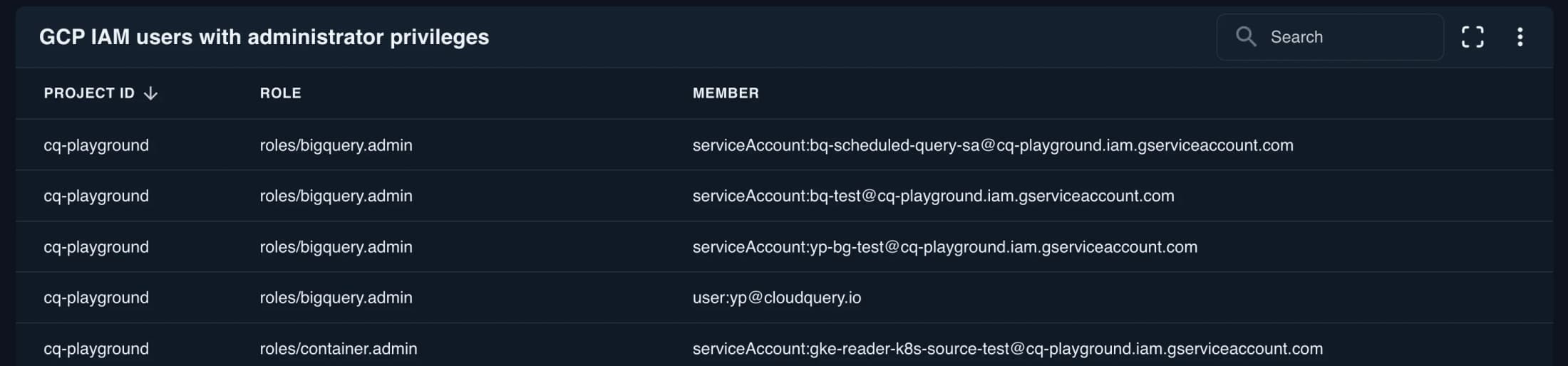
GCP IAM users with administrator privileges
Identifies accounts with excessive permissions in Google Cloud. Ensure these powerful accounts follow proper security controls.
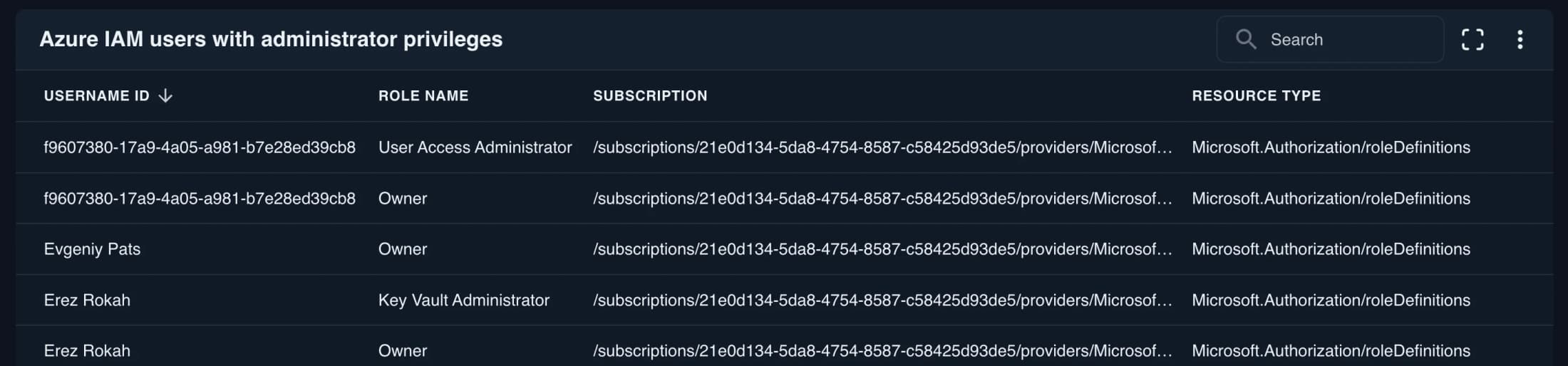
Azure IAM users with administrator privileges
Lists which accounts have privileged access in Microsoft Azure. Verify these powerful accounts are limited to appropriate users.