Azure: Attack Surface Security Posture report documentation
Expose misconfigurations and internet-facing risks in your Azure cloud environment to reduce your attack surface.
About this report
Discover security weaknesses in your Azure environment that attackers could exploit to gain unauthorized access. Your security team will identify risky network rules, authentication issues, and public resources that need immediate hardening to protect your Microsoft cloud resources.
Key questions
- What are my most critical Azure security vulnerabilities?
- Which Azure resources are unnecessarily exposed to the internet?
- Are my Azure virtual machines properly secured?
- How can I reduce my attack surface in Microsoft Azure?
Visualizations in the report
VM Access: Unrestricted ingress network rules
Flags virtual machines with overly permissive inbound firewall rules. Attackers actively scan for these entry points, making them a priority for remediation.
VM Access: Unrestricted egress network rules
Shows VMs with unlimited outbound access permissions. These configurations could allow data exfiltration or command-and-control connections if a system is compromised.
VMs with Password Authentication
Lists virtual machines using password-based access instead of stronger key-based authentication. Credentials can be stolen or brute-forced, creating unnecessary risk.
Public Databases
Identifies database servers directly reachable from the internet. This dangerous configuration violates security best practices for sensitive data protection.
Public Kubernetes Node Pools
Reveals container orchestration nodes exposed to the public network. These misconfigurations create unnecessary risk for your containerized applications.
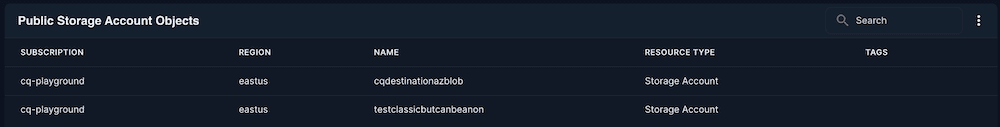
Public Storage Account Objects
Shows storage blobs and files accessible without authentication. Quickly find and fix potential data exposures before sensitive information leaks.