AWS Security Best Practices report documentation
Identify common AWS misconfigurations that violate best practices and put your environment at risk.
About this report
Quickly discover common security misconfigurations that leave your AWS environment vulnerable to attack. Security teams gain a prioritized view of essential hardening actions across IAM, network, storage, and compute resources that will immediately improve your security posture.
Key questions
- What are my most urgent AWS security vulnerabilities?
- Which AWS security best practices am I not following?
- How can I reduce my attack surface in AWS?
- Are my critical AWS resources properly secured?
Visualizations in the report
Root users without MFA Enabled
Identifies your most powerful credentials lacking critical protection. The root user can do anything in an AWS account, making MFA absolutely essential for these credentials.
S3 public buckets
Highlights storage that anyone on the internet can access. Prevent accidental data exposure by quickly finding and securing these vulnerable resources.
EBS unencrypted volumes
Maps storage volumes missing data protection. This visualization helps you find sensitive data that might be exposed if the underlying storage is compromised.
Publicly Accessible RDS Instances
Shows database servers exposed directly to the internet. Immediately identify these high-risk configurations that violate security best practices.
Unencrypted RDS databases
Flags databases operating without data protection. Ensure sensitive information is protected from theft if backup files or snapshots are compromised.
Security groups allowing access from the public network
Reveals overly permissive network rules. Quickly find and fix firewall configurations that permit traffic from any IP address.
EC2 instances authorizing SSH from anywhere
Identifies servers with dangerously open administrative access. These configurations allow attackers to attempt brute-force attacks from anywhere on the internet.
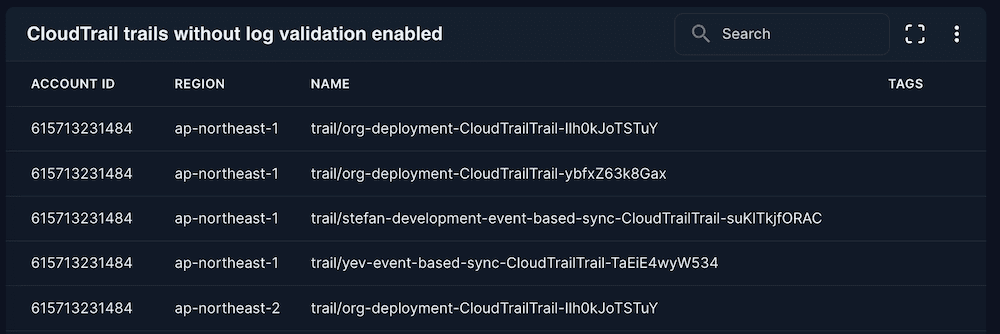
CloudTrail trails without log validation enabled
Shows logging configurations vulnerable to tampering. Ensure the integrity of your security audit data by identifying logs that could be modified to hide attacker activity.
IAM inactive users
Lists dormant user accounts that should be disabled. Reduce your attack surface by cleaning up these unnecessary access points.
IAM unused roles
Highlights permission sets that aren't being utilized. These unnecessary permissions could be exploited if an account is compromised.
AWS Lambda functions with deprecated runtimes
Reveals serverless functions running outdated environments. Functions using deprecated runtimes often contain unpatched security vulnerabilities.